The new feature was introduced in the Windows 10 Anniversary Update to allow IT-administrators to configure automatic VPN connection profiles. As mentioned earlier, Always On VPN has some important advantages over DirectAccess. For instance, Always On VPN can use both IPv4 and IPv6. So, if you have some apprehensions about the future viability of DirectAccess, and if you meet all of the requirements to support Always On VPN with Windows 10, then perhaps switching to the latter is the right choice.
Always On VPN for Windows 11/10 client computers
This tutorial walks you through the steps to deploy Remote Access Always On VPN connections for remote client computers that are running Windows 11/10.
Before proceeding any further, ensure you have the following in place:
An Active Directory domain infrastructure, including one or more Domain Name System (DNS) servers.Public Key Infrastructure (PKI) and Active Directory Certificate Services (AD CS).
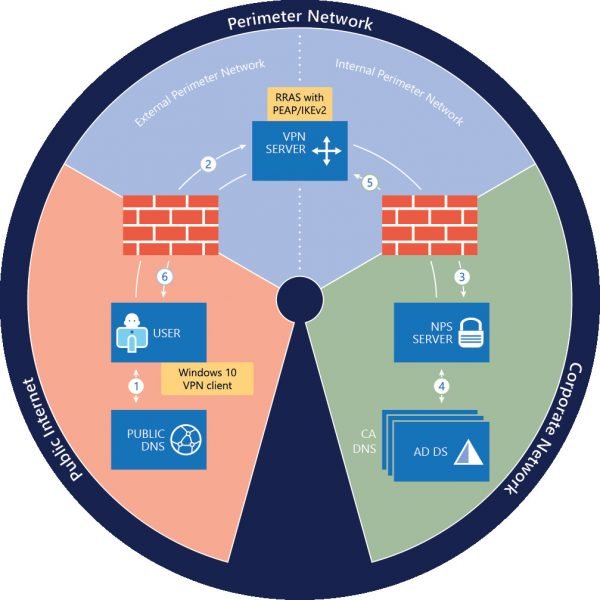
To begin Remote Access Always On VPN Deployment, install a new Remote Access server that is running Windows Server 2016. Next, perform the following actions with the VPN Server: After you complete the above procedure, install and configure Remote Access as a single-tenant VPN RAS Gateway for point-to-site VPN connections from remote computers. Try configuring Remote Access as a RADIUS Client so that it is in a position to send connection requests to the organization NPS server for processing. Enroll and validate the VPN server certificate from your certification authority (CA).
NPS Server
If you are not aware, it is the server that is installed on your organization/corporate network. It is necessary to configure this server as a RADIUS server so as to enable it to receive connection requests from the VPN server. Once the NPS server starts receiving requests, it processes the connection requests and performs authorization and authentication steps before sending an Access-Accept or Access-Reject message to the VPN Server.
AD DS Server
The server is an on-premises Active Directory domain, which hosts on-premises user accounts. It requires you to set up the following items on the domain controller. The Certification Authority (CA) Server is a certification authority that is running Active Directory Certificate Services. The CA enrolls certificates that are used for PEAP client-server authentication and creates certificates based on certificate templates. So, first, you need to create certificate templates on the CA. The remote users that are allowed to connect to your organization network must have a user account in AD DS. Also, make sure that your firewalls allow the traffic that is necessary for both VPN and RADIUS communications to function correctly. Apart from having these server components in place, ensure that the client computers you configure to use VPN are running Windows 11/10. The Windows VPN client is highly configurable and offers many options. This guide is designed for deploying Always On VPN with the Remote Access server role on an on-premises organization network. Please do not attempt to deploy Remote Access on a virtual machine (VM) in Microsoft Azure. For complete details and configuration steps, you can refer to this Microsoft Document. Also read: How to setup & use AutoVPN in Windows to connect remotely.